Pdf Digital Signature Validated but While Sending Attachment Again It Is Showing Not Valid
Past default, all 64-bit Windows versions foreclose the installation of devices drivers that are not signed with a valid digital signature. Unsigned drivers are blocked by the operating system. A digital signature ensures that the commuter has been released by a trusted programmer or vendor, and its lawmaking hasn't been modified.
There are several ways to disable driver signature verification for the unsigned drivers in Windows (using a GPO, a test kicking mode, etc). Today we'll testify how to sign any unsigned driver for Windows x64 (the guide is applicative for Windows 11, 10, 8.1, and 7).
Contents:
- Create a Self-Signed Driver Certificate
- Creating a Catalog File (CAT) for Signing a Driver Packet
- Signing the Driver Package with a Self-Signed Certificate
- Installing a Self-Signed Driver on Windows
- User-Style and Kernel-Fashion Drivers in Windows
Suppose you have a certain unsigned device driver (without digital signature) for Windows ten x64. In this example, it is the driver for a quite one-time graphics card. The annal with drivers for your Windows version has been downloaded from the vendor's website (I was able to find the video driver version only for Windows Vista x64) and its contents have been extracted to the c:\tools\drv1\. Let'due south try to install the driver by adding it to the Windows driver store with a built-in pnputil tool:
Pnputil –a c:\tools\drv1\xg20gr.inf
Note. This command and all the next ones must be run in the command prompt as an administrator.
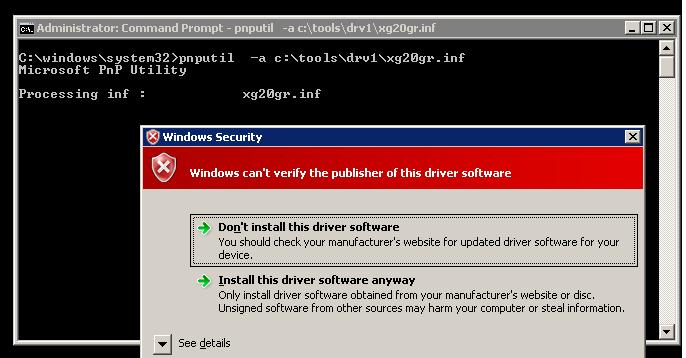
During driver installation, Windows 7 displays a warning that the operating system can't verify the digital signature of this driver:
Windows can't verify the publisher of this driver software.
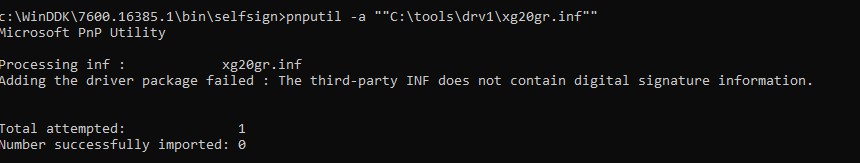
In Windows ten (21H2) this warning doesn't appear, but an error appears in the console:
Processing inf: xg20gr.inf Adding the commuter package failed: The third-political party INF does not contain digital signature information.
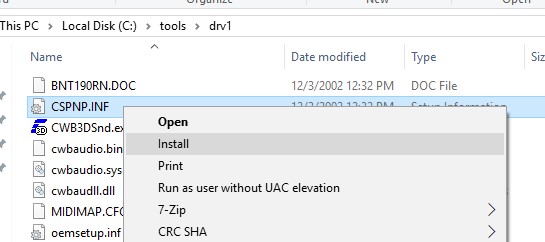
If you right-click on the inf driver file and select Install when installing a driver from File Explorer, you receive an mistake:
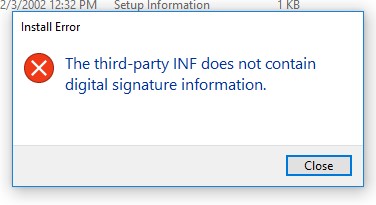
The third-party INF does not incorporate digital signature information.
Let's try to sign this driver with a cocky-signed certificate.
To generate a signature and sign the driver, y'all need to download and install the following Windows awarding development tools:
- Windows SDK (Software Development Kit) or Microsoft Visual Studio 2005+ for your Windows version. Install the Windows SDK Signing tools for Desktop package which contains the
signtool.exe; - Windows Driver Kit (WDK) — https://docs.microsoft.com/en-u.s.a./windows-hardware/drivers/download-the-wdk
Create a Cocky-Signed Commuter Certificate
Create a C:\DriverCert folder at the root of the organisation drive.
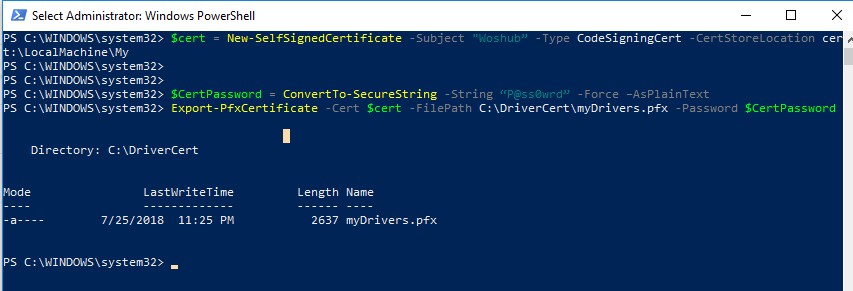
You can use the New-SelfSifgnedCertificate PowerShell cmdlet to create a code signing certificate. In this example, we will create a self-signed certificate with a validity period of 3 years.
$todaydate = Go-Date
$add3year = $todaydate.AddYears(3)
$cert = New-SelfSignedCertificate -Bailiwick "WOSHUB" -Blazon CodeSigningCert -CertStoreLocation cert:\LocalMachine\My -notafter $add3year
Then you demand to export this document to a pfx file with a password:
$CertPassword = ConvertTo-SecureString -String "P@ss0wrd" -Forcefulness –AsPlainText
Consign-PfxCertificate -Cert $cert -FilePath C:\DriverCert\myDrivers.pfx -Password $CertPassword
Since the certificate we created is self-signed, Windows doesn't trust it by default. When you check the certificate store with the Sigcheck utility, this document will be displayed as untrusted, because it is non listed in the listing of Microsoft Trusted Root Certificates (this list needs to be updated periodically).
Now you need to add the certificate to the Trusted Root store and to the Trusted Publisher certificates:
$certFile = Export-Certificate -Cert $cert -FilePath C:\DriverCert\drivecert.cer
Import-Certificate -CertStoreLocation Cert:\LocalMachine\AuthRoot -FilePath $certFile.FullName
Import-Certificate -CertStoreLocation Cert:\LocalMachine\TrustedPublisher -FilePath $certFile.FullName
In previous versions of Windows, you must utilize the makecert.exe tool from the Windows Software Evolution Kit (SDK) to generate self-signed certificates. In this case, the commands to create a certificate will wait similar this:
cd "C:\Program Files (x86)\Microsoft SDKs\Windows\v7.1\bin"
Create a self-signed certificate and private central, that is issued, for case, for the company WinOSHub:
makecert -r -sv C:\DriverCert\myDrivers.pvk -n CN="WinOSHub" C:\DriverCert\myDrivers.cer
During the creation of the document, the tool volition prompt you lot to specify a password for the key. Let it be P@ss0wrd.
Create a public fundamental for a publisher certificate (PKSC) we have created earlier:
cert2spc C:\DriverCert\myDrivers.cer C:\DriverCert\myDrivers.spc
Combine the public key (.spc) and the individual key (.pvk) in a single certificate file with format Personal Data Exchange (.pfx):
pvk2pfx -pvk C:\DriverCert\myDrivers.pvk -pi P@ss0wrd -spc C:\DriverCert\myDrivers.spc -pfx C:\DriverCert\myDrivers.pfx -po P@ss0wrd
Add together the document to trusted:
certmgr.exe -add C:\DriverCert\myDrivers.cer -south -r localMachine ROOT
certmgr.exe -add C:\DriverCert\myDrivers.cer -s -r localMachine TRUSTEDPUBLISHER
You can centrally deploy this certificate to client computers using Grouping Policy in an AD domain.
Open the auto'due south local certificate management snap-in (certlm.msc) and verify that your certificate is in the Trusted Publishers and Trusted Root Certification Authorities.
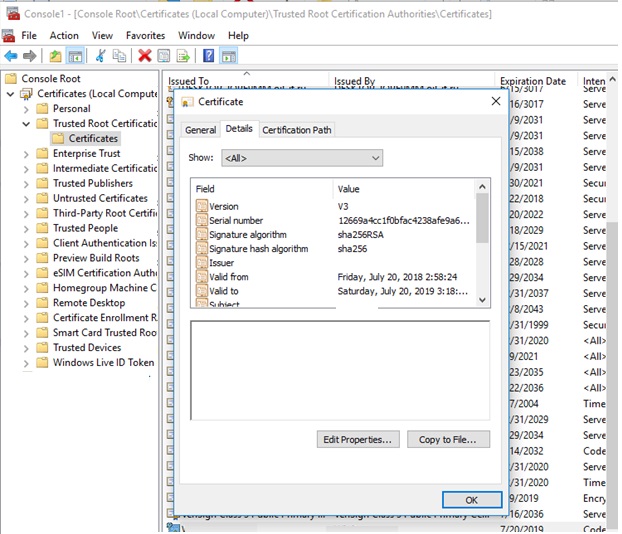
Note. Even though the certificate has a limited validity menstruum, the expiration of the CodeSigning certificate means that you can't create new signatures. The validity of the driver already signed by this certificate is unlimited (or old signatures are valid during the specified timestamp).
Creating a Catalog File (True cat) for Signing a Driver Packet
Create the directory C:\DriverCert\xg20 and copy all files from the folder into which the driver from the archive has been originally extracted (c:\tools\drv1\). Make sure that there are files with the extensions .sys and .inf amongst these files (in our case, they are xg20grp.sys and xg20gr.inf).
md C:\DriverCert\xg
xcopy c:\tools\drv1\ C:\DriverCert\xg /i /c /k /east /r /y
Go to the directory:
cd "C:\Program Files (x86)\Windows Kits\10\bin\10.0.22000.0\x86"
Generate a CAT file (contains information about all the files in the commuter package) on the base of operations of the INF file. The inf2cat.exe tool (from the Windows Driver Kit, WDK) allows yous to generate a True cat file for your platform:
inf2cat.exe /driver:"C:\DriverCert\xg20" /os:7_X64 /verbose
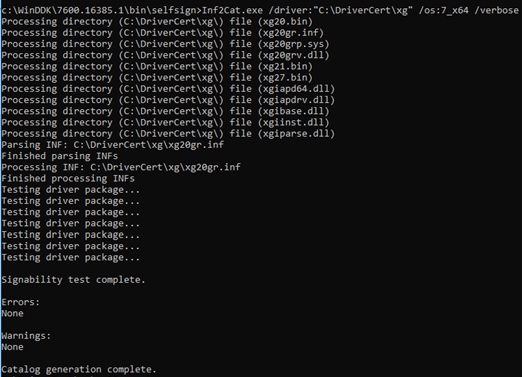
To make sure that the process was correct, check that the file C:\DriverCert\xg\xg20gr.true cat has appeared in the target directory, and there are messages in the log:
Signability examination complete.
and
Catalog generation complete.
Note. In my instance the command Inf2Cat.exe returned an error:
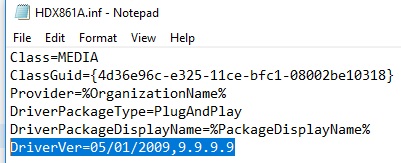
Signability test failed. Errors: 22.9.7: DriverVer gear up to incorrect date (must be postdated to 4/21/2009 for newest OS) in \hdx861a.inf
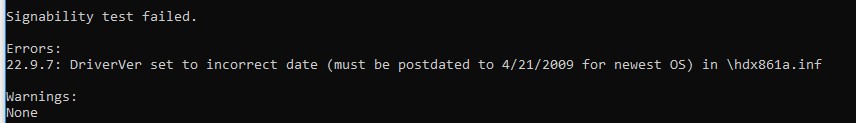
To fix the error, find the line with DriverVer = in the [Version] section and supplant it with:
DriverVer=05/01/2009,9.9.9.9
If you get an fault Missing AMD64 CatalogFile entry (for x64) or Missing 32-bit CatalogFile entry, then add the line CatalogFile=xg20gr.cat to the [Version] section of the .inf file.
Signing the Driver Parcel with a Self-Signed Certificate
Get to the following folder:
cd "C:\Programme Files (x86)\Windows Kits\10\bin\10.0.22000.0\x64"
Sign the driver bundle (set of files) with the certificate yous have created earlier using Verisign as a timestamp service. The following control volition sign the True cat file with a digital signature using a certificate stored in a password-protected .pfx file:
signtool sign /f C:\DriverCert\myDrivers.pfx /p P@ss0wrd /t http://timestamp.verisign.com/scripts/timstamp.dll /v C:\DriverCert\xg20\xg20gr.true cat
On modern versions of Windows 10 and Windows 11, running this command will event in an error:
SignTool Error: No file digest algorithm specified. Please specify the digest algorithm with the /fd flag. Using /fd SHA256 is recommended and more secure than SHA1. Calling signtool with /fd sha1 is equivalent to the previous beliefs. In society to select the hash algorithm used in the signing certificate's signature, employ the /fd certHash option.
You demand to apply another command:
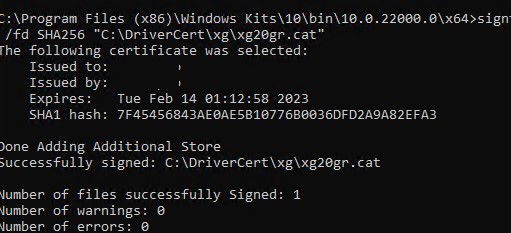
signtool sign /tr http://timestamp.digicert.com /td SHA256 /v /f C:\DriverCert\myDrivers.pfx /p P@ss0wrd "C:\DriverCert\xg\xg20gr.cat"
If the control returns an error SignTool Mistake: An unexpected internal fault has occurred, or Error information: SignerTimeStamp() failed. (-2147012865/0x80072eff), try a different timestamp server URL. Try whatsoever of the list:
http://timestamp.comodoca.com/authenticode http://timestamp.globalsign.com/scripts/timstamp.dll http://timestamp.verisign.com/scripts/timstamp.dll http://tsa.starfieldtech.com http://world wide web.startssl.com/timestamp
If the CAT file is signed successfully, the following message should appear:
Successfully signed: C:\DriverCert\xg\xg20gr.cat Number of files successfully Signed: i
The commuter's digital signature is contained in the .cat file referenced in the .inf file. You tin bank check the digital signature of the driver in the true cat file using the following command:
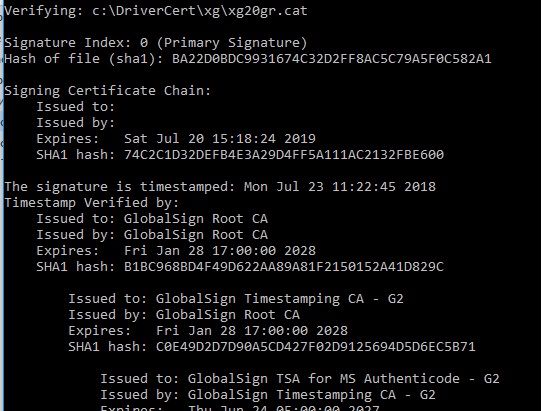
SignTool verify /v /pa c:\DriverCert\xg\xg20gr.true cat
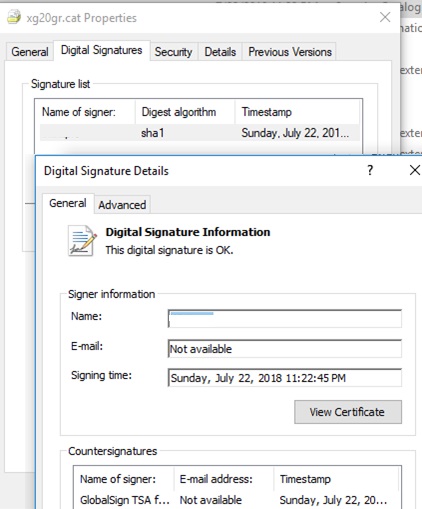
Y'all tin can too see data about the certificate in the backdrop of the True cat file on the Digital Signatures tab.
If the certificate is not trusted (or has not been added to the Trusted Root Certificate Store), then an error will appear when running the SignTool verify command:
SignTool Error: A certificate chain processed, just terminated in a root certificate which is not trusted by the trust provider.
The CAT file contains digital signatures (thumbprints) of all the files that are in the driver directory (files listed in the INF file in the CopyFiles section). If any of these files have been changed, then the checksum of the files volition not match the data in the CAT file, and, every bit a result, the installation of such a commuter volition fail.
Installing a Self-Signed Commuter on Windows
Try to install the driver we accept signed over again using the command:
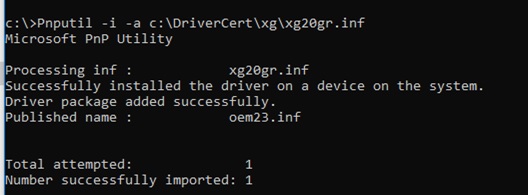
Pnputil –i –a C:\DriverCert\xg20\xg20gr.inf
Now you won't see the warning most the missing digital signature of the driver.
Successfully installed the driver on a device on the system.
Commuter package added successfully.
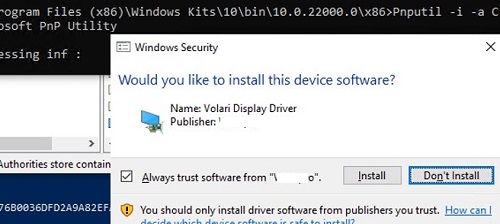
The following warning appears in Windows ten and xi:
Would y'all similar to install this device software?
Click "Install" to install the driver package on Windows.
If for some reason the commuter is not installed, a detailed driver installation log is contained in the file C:\Windows\inf\setupapi.dev.log. This log file allows y'all to become more information about the commuter installation errors. In most cases, there is a "Commuter bundle failed signature validation" error. Most likely this means that the driver's document is non added to the trusted certificates store.
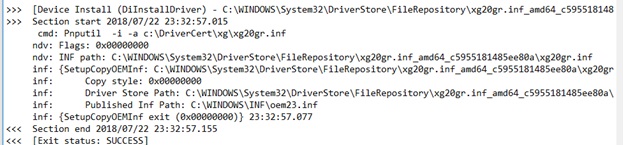
If the driver installation was successful, the setupapi.dev.log file should contain the following lines:
>>> [Device Install (DiInstallDriver) - C:\WINDOWS\System32\DriverStore\FileRepository\xg20gr.inf_amd64_c5955181214aa12b\xg20gr.inf] >>> Section showtime 2018/07/22 23:32:57.015 cmd: Pnputil -i -a c:\DriverCert\xg\xg20gr.inf ndv: Flags: 0x00000000 ndv: INF path: C:\WINDOWS\System32\DriverStore\FileRepository\xg20gr.inf_amd64_c5955181214aa12b\xg20gr.inf inf: {SetupCopyOEMInf: C:\WINDOWS\System32\DriverStore\FileRepository\xg20gr.inf_amd64_c5955181214aa12b\xg20gr.inf} 13:23:37.046 inf: Re-create style: 0x00000000 inf: Driver Store Path: C:\WINDOWS\System32\DriverStore\FileRepository\xg20gr.inf_amd64_c5955181214aa12b\xg20gr.inf inf: Published Inf Path: C:\WINDOWS\INF\oem23.inf inf: {SetupCopyOEMInf exit (0x00000000)} 13:23:37.077 <<< Section end 2018/07/22 13:23:37.155 <<< [Go out status: SUCCESS] User-Mode and Kernel-Mode Drivers in Windows
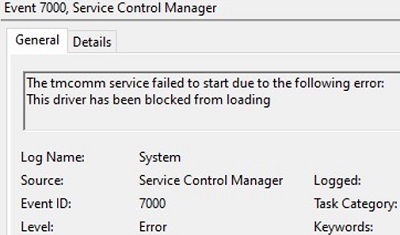
Let me remind yous that in Windows the driver can be executed in a kernel-mode or in a user mode. Kernel-mode drivers signed this way won't load when Windows boots on the UEFI device with Secure Boot enabled with the error:
Outcome ID: 7000 ERROR_DRIVER_BLOCKED 1275 (0x4FB) This commuter has been blocked from loading.
You tin can bank check if Secure Boot way is enabled using the PowerShell command:
Confirm-SecureBootUEFI
All kernel-mode drivers loaded with SecureBoot enabled must be signed during the Microsoft certification procedure (WHQL – Windows Hardware Quality Lab). The reason is that when the kernel is loaded, UEFI cannot verify the certificates in the Windows local machine certificate store.
SignTool Error: Signing Cert does non chain to a Microsoft Lawmaking Verification Root.
Microsoft requires mandatory third-political party driver certification under the Windows Hardware Compatibility Program starting with Windows 10 1607.
Self-signed user-manner drivers (usually printers, scanners, plotters, etc.) volition piece of work even with SecureBoot enabled.
For kernel-manner drivers, you will have to disable digital signature verification and kicking Windows in a test fashion with the bcdedit.exe commands:
bcdedit.exe /set /nointegritychecks on
bcdedit.exe /set testsigning ON
Source: http://woshub.com/how-to-sign-an-unsigned-driver-for-windows-7-x64/
0 Response to "Pdf Digital Signature Validated but While Sending Attachment Again It Is Showing Not Valid"
Post a Comment